As we have now moved into Q2 we have already seen the continued trend in the media of companies that have become victim to Ransomware, with some businesses turning to paying the ransom and relying on cyber insurance to cover the costs.
In March, we saw Acer become victim of the highest ever ransom demand of a reported $50 Million ransom after being subject to the REvil ransomware variant. Throughout March we saw a disturbing trend in schools being targeted, which at a time when we are relying on digital systems for home schooling it is a national and cultural topic.
The most despicable ransomware attack I think we have seen this year is where REvil or Ryuk was seen to be targeting hospitals and threatening human life and treatment. That is a basic right that the Geneva convention looks to protect during war, so to be attacking a such a critical basic human right is difficult to see.
So, at Bridewell, we have reviewed our Cyber Threat Intelligence database to give you an insight into the top ransomware threats, their targets and techniques used mapped to the Mitre Att&ck framework. We are hoping that this information provides insight to aid prevention and detection of these threats. If it comes to recovery, then make sure you have an active backup.
What is the Mitre Att&ck framework?
The Mitre Att&ack framework is a matrix of tactics, techniques, and procedures (TTPs) used by security teams, threat hunters, red and blue teamers alike to better classify and assess cyber risk and kill chain activities.
The goal of the framework is to improve post-compromise detection of bad actors within an environment by offering insight into the actions an attacker may have taken to get in and move around. The framework helps answer those questions but also provides an awareness of the threats that face an organisations security and IT posture. Used correctly, the Mitre Att&ck framework can help organisations identify holes in prevention and detection and plan their protection.
For more information on the Att&ck framework and how to start using it, an ebook is available here.
Bridewell's Top 4 Ransomware of Q1 2021
So, to come up with this list, we have looked at those strains of Ransomware that have triggered our threat intelligence database the most over the previous quarter and selected those with both a high volume, but also damaging impact, technically or commercially.
DarkSide Ransomware
First up is DarkSide. First observed in August 2020, DarkSide operates as a ransomware-as-a-service (RaaS) variant, that is known to conduct highly targeted attacks against large organisations, claiming to only attack those companies that can afford the ransomware. After initial access, DarkSide moves laterally through a network and exfiltrates unencrypted data before encrypting at the file level. Following the trend of other recent ransomware variants, DarkSide maintain a data leak website to expose the data upon on payment. We categorise the variant as high risk.
Geographically, DarkSide predominately targets US and Canadian companies and has been seen to target industrial goods and services, Financial and Legal sectors the most. Most recently, at the time of writing, their leak site would suggest that law firm Cuddy & Feder LLP were their most recent victim and obtained over 120GB or sensitive data and released the information within the last week.
DarkSide Mitre Att&ck TTPs
System Services: Service Execution (T1569)
Process Injection: Dynamic-link Library Injection (T1055)
Abuse Elevation Control Mechanism: Bypass User Access Control (T1548)
File Permissions Modification (T1222)
Data Encrypted for Impact (T1486)
Inhibit System Recovery (T1490)
System Information Discovery (T1082)
Compile After Delivery (T1500)
Credentials in Registry (T1214)
It is noted that there are similarities between DarkSide and the Revil ransomware variant, but nothing has been confirmed about the overlap.
Avaddon Ransomware
Next, we have Avaddon which is another ransomware-as-a-service variant that has been identified in the wild since June 2020. They charge no fee to use the software but collect a 35% of the ransom fee paid, which is usually only between USD 150 and 300.
The variant is growing in the number of threat intelligence triggers such as breach identification, with 28 in 2020 and already 56 seen in 2021. Avaddon is spread through phsishing emails, exploiting both fear and curiosity of the recipients, but importantly, it has been observed that Avaddon has been known to evade email security solutions, making its threat level high. The malicious email comes with a Javascript attached, masquerading as a photo, which when opened launches PowerShell to run without warning or prompts to download an executable that then causes damage and leaves a ransom note.
Threat intelligence from the operators leak website suggest that Mevion Medical Systems Inc was targeted within the last two weeks with industrial goods and services, technology and healthcare organisations in the US and Europe being a favourite target.
Avaddon Mitre Att&ck TTPs
The following techniques have been witnessed when investigating the Avaddon attacks. Using the information below to ensure that you have the detections in place to identify any stage and ideally prevent initial access will drastically help reduce the impact and cost of an attack.
Spearphishing Attachment (T1193)
Windows Management Instrumentation (T1047)
Kernel Modules and Extensions (T1215)
Registry Run Keys/Startup Folder (T1060)
File and Directory Discovery (T1083)
Virtualization/Sandbox Evasion (T1497)
System Network Configuration Discovery (T1016)
Peripheral Device Discovery (T1120)
Data Encrypted for Impact (T1486)
Inhibit System Recovery (T1490)
Conti Ransomware
Making second place on our list is Conti. Conti uses a high number of threads to perform encryption making the attack period much shorter, making this a high-risk variant. Conti has also been in operation since December 2019 and is believed to be derived from the “Ryuk” ransomware variant.
Often deployed using the “TrickBot” infrastructure, Conti is designed to be operated by the attacker rather than an automated process which may suggest it’s found to be used in a more targeted method in the selection of its victims. The last identified attack was within the last week and Klenda Austerman LLP was the victim.
Targeted organizations operate in several sectors. The most heavily affected are construction, manufacturing, and retail. Other affected industries include critical national infrastructure, including government, distribution, utilities, IT, healthcare, financial services and oil and gas. Conti operations do not appear to favor any specific geographies and attacks have been reported affecting organizations in the US, the UK, Spain, France, Germany, and Canada.
Conti Mitre Att&ck TTPs
The following techniques have been witnessed when investigating the Conti attacks. Using the information below to ensure that you have the detections in place to identify any stage and ideally prevent initial access will drastically help reduce the impact and cost of an attack.
System Services: Service Execution (T1569)
Abuse Elevation Control Mechanism: Bypass User Access Control (T1548)
Create or Modify System Process (T1543)
Exploitation for Privilege Escalation (T1068)
Command and Scripting Interpreter (T1059)
File Permissions Modification (T1222)
Data Encrypted for Impact (T1486)
Inhibit System Recovery (T1490)
System Information Discovery (T1082)
Windows Management Instrumentation (T1047)
Indicator Removal on Host (T1070)
Remote System Discovery (T1018)
Credentials in Registry (T1214)
Sodinokibi AKA REvil Ransomware
The last on our list is in our opinion, a very high risk both in terms of age, numbers, but the impact and cost of a successful attack and that is Sodinokibi, also known as REvil or Sodin. Since first being detected in April 2019 Sodinokibi is attributed to the highest known ransom to date with the recent Acer attack and a reported $50 Million ransom fee.
Sodinokibi also operates as a ransomware-as-a-service and has been linked to several affiliated parties who carry out the attacks and spread the ransomware. The initial access has been established using various method’s including phishing and malvertising but they have also focused on compromising vulnerabilities found in Oracle WebLogic Server (CVE-2019-2725) and the zero-day vulnerability in Windows (CVE-2018-8453). In addition, Sodinokibi operators have also breached managed service providers (MSPs) to deploy the ransomware on the MSPs’ customers, making the supply chain dangerous.
Initial attacks focused on users in Asia but Sodinokibi’s attacks have expanded to target entities globally. Sodinokibi victims include organisations in healthcare, legal services, technology, government, retail, banks, and other financial services. The operators of the GandCrab ransomware announced the variant would be retired on 31 May 2019; reported activity involving Sodinokibi became more frequent following the announcement.
Sodinokibi Mitre Att&ck TTPs
The following techniques have been witnessed when investigating the Sodinokibi attacks. Using the information below to ensure that you have the detections in place to identify any stage and ideally prevent initial access will drastically help reduce the impact and cost of an attack.
Obfuscated Files or Information (T1027)
Command and Scripting Interpreter (T1059)
Remote Desktop Protocol (T1076)
External Remote Services (T1133)
Exploit Public-Facing Application (T1190)
Spearphishing Attachment (T1193)
Supply Chain Compromise (T1195)
Data Encrypted for Impact (T1486)
Inhibit System Recovery (T1490)
Ransomware Growth
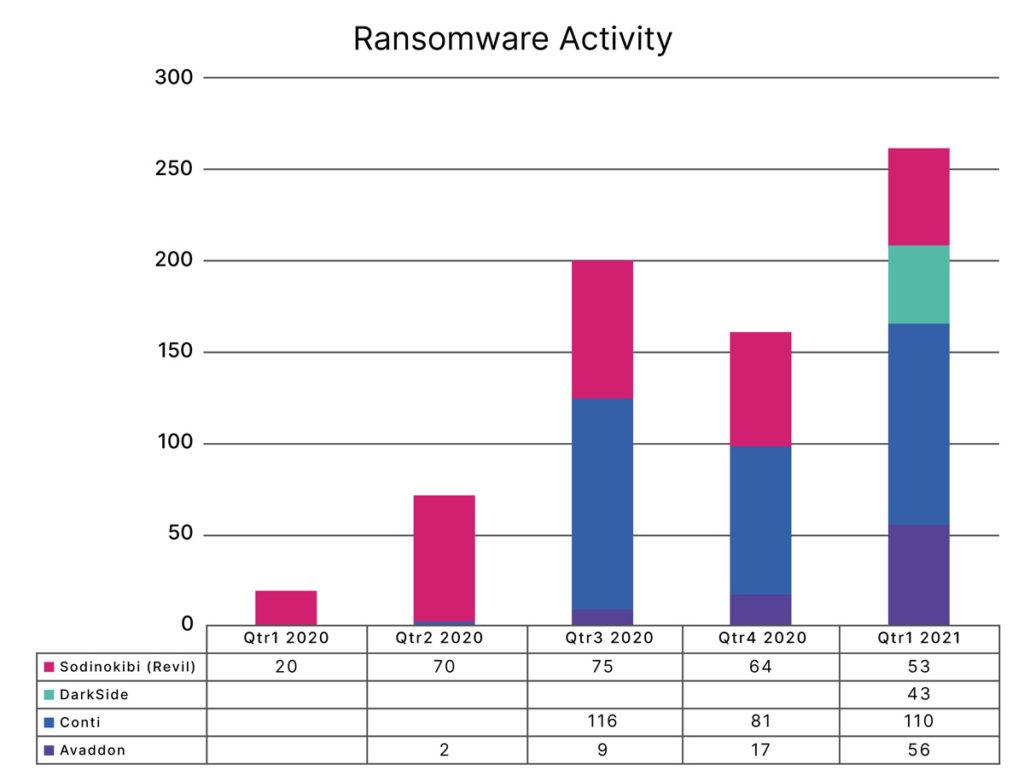
We have known that ransomware is maintaining its position as a leading threat, and projections were that after the initial increase in activity following the COVID led disruptions, that it would continue to grow in 2021. The graph below demonstrates their volumes and over the last five quarters and the trends are showing only one thing, that ransomware needs to remain a top threat to your digitally enabled business and there is no end in sight.
Whitepaper: Human Operated Ransomware
A fantastic new whitepaper which deep dives into:
- The types of ransomware attack currently prevalent
- The major ransomware players
- An in-depth look at human operated ransomware and its complexity
- How to protect against an attack
- How to detect, respond to, and recover from an attack


 Blogs
Blogs