Public Exploits released for CVE-2019-19781 (Citrix ADC / Netscaler)
Base Score: 9.8 CRITICAL [i]
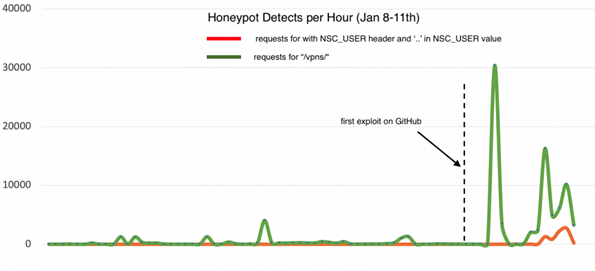
The vulnerability was first published by Citrix on the 17th December 2019 and the first working public exploit released on GitHub overnight on the 10th January 2020. The vulnerability was identified in Citrix Application Delivery Controller (ADC) formerly known as NetScaler ADC and Citrix Gateway formerly known as NetScaler Gateway where, if exploited, could allow an unauthenticated attacker to perform arbitrary code execution.
The available public exploits allow the attackers to connect to a reverse shell on the target machine, allowing them to then run further malicious code in order to take full control of the machine and perform further actions such as installing ransomware or cryptocurrency miners.
Citrix have listed the following products as being affected [iii]
- Citrix ADC and Citrix Gateway version 13.0 all supported builds
- Citrix ADC and NetScaler Gateway version 12.1 all supported builds
- Citrix ADC and NetScaler Gateway version 12.0 all supported builds
- Citrix ADC and NetScaler Gateway version 11.1 all supported builds
- Citrix NetScaler ADC and NetScaler Gateway version 10.5 all supported builds
Note: Legacy products may still be affected by this CVE. Please perform the relevant checks as detailed below to test if the legacy version is vulnerable.
How to validate your exposure: [iv]
The following request will test whether your Citrix appliance is affected by the working public exploit. The appliance policy should not allow access to /vpns/ or /../ which are required for the public exploit to work. Enter the following request in your terminal or command prompt:
‘curl https://host/vpn/../vpns/cfg/smb.conf –path-as-is’
If you receive a 403 response or the request returns the Citrix website and NOT the smb.conf contents then you are patched against this vulnerability.
If you can see the results of smb.conf, then you are vulnerable.
Note: If you receive a certificate error in the response you will need to include the flag ‘—proxy-insecure’ to control the certificate verification.
Additionally, The Cyber security and Infrastructure Agency (CISA) have released a free tool to test whether a Citrix ADS or Citrix Gateway is vulnerable to CVE-2019-19781 which can be found here…
Mitigation steps provided by Citrix:
Detection rule by Sigma:
Netscaler RCE Forensics
- [i] https://nvd.nist.gov/vuln/detail/CVE-2019-19781
- [ii] https://isc.sans.edu/forums/diary/Citrix+ADC+Exploits+are+Public+and+Heavily+Used+Attempts+to+Install+Backdoor/25700
- [iii] https://support.citrix.com/article/CTX267027
- [iv] https://github.com/trustedsec/cve-2019-19781



 Blogs
Blogs