Purple Teaming is the coming together of offensive and defensive security teams with the common goal of identifying, addressing, and reducing risk to the business.
Traditionally Red and Blue teams have operated in silos. The Purple team concept aims to address this disconnect and is a natural evolution for organisations looking to utilise more advanced security testing such as Red team engagements.
There is still very much a place for Red Teaming and adversary emulation as these capabilities provide the highest realism and provide businesses a clear picture of the current state of their security.
However, Purple Teaming brings additional value by improving an organisation’s knowledge of both red and blue teams and upskilling individual capabilities.
To achieve the goal of reducing business risk the Purple Team sets out to understand the threats faced by the organisation. Remember to consider that threats can be defined as anyone with the capability, intent, and opportunity to do harm to your business.
You will save a great deal of time and effort by focusing on the threats and attacks that can cause the most impact to your business.
A threat intelligence program should support development of your Purple Team strategy and individual assessments. Firstly, it identifies groups and actors who present the greatest risk to the business – mapping their tactics, techniques, and procedures (TTP’s) to attack kill chains.
Once the threats are understood and prioritised, the Purple Team will plan the assessment and emulate identified threats using associated kill chains and TTPs commonly used to perform the attack.
How to use MITRE ATT&CK
MITRE ATT&CK is a cloud-hosted database of adversary tactics and techniques that are leveraged by threat groups to perform their attacks. Based on real-world observations, it is a great resource to assist in threat modeling and building out Purple Team assessments that address the current commonly-used tactics and techniques.
To plan an assessment you should start looking for threat groups or tactics that relate to your business using the MITRE ATT&CK website.
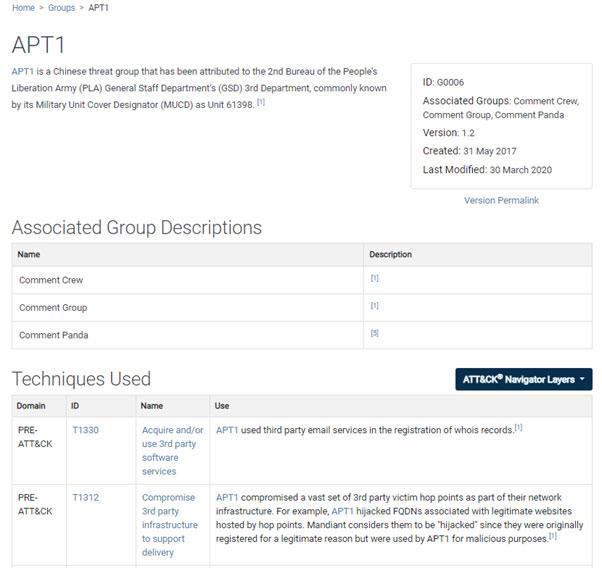
The image below depicts a profile on APT1 and includes the techniques and software the group has been observed using. Bear in mind there is nothing stopping them using other techniques or tools, however, these are indicators associated with the group from previous intrusion analysis.
MITRE also provides an ATT&CK navigator application that allows you to render an overlay of the techniques used by each threat group. This visualisation can be extremely useful to the Purple Team as part of your framework and helps you stage the attack simulations. An example of an overlay for APT 1 is illustrated below:
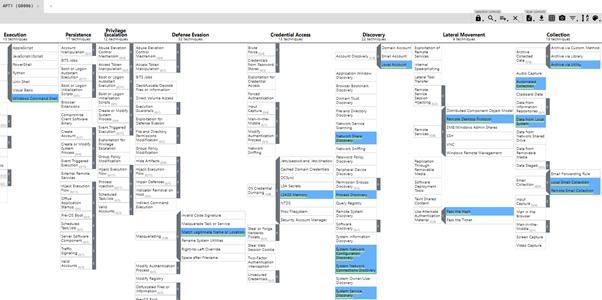
Using the overlay, the Purple Team can start to plan an assessment, establishing the required data sources, infrastructure and TTPs to perform the assessment.
The goal of the Purple assessment itself is to test and improve the organisation’s capabilities to prevent, detect and respond to attacks through deep collaboration with those performing the attacks.
This enables the blue team to observe the attacks as they happen and adjust instrumentation to detect and address the attack, or a variation, to ensure analytics cannot be easily bypassed by modifying atomic indicators.
Working side-by-side, the Purple Team leverage the Red Team’s offensive knowledge to understand the attack techniques in greater detail, again improving the ability to recalibrate detection and prevention controls.
This method of assessment enables continuous improvement and provides real world validation of your security controls.
Types of Assessment
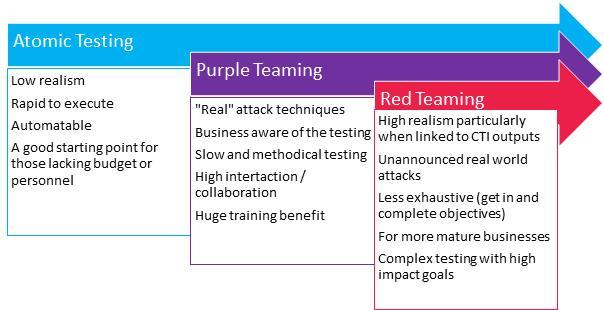
There are two main types of Purple Team assessments. The first is Simulation Testing or Atomic Testing and the second is Purple Teaming. Atomic Testing is essentially the use of scripted techniques that are easy to run and automate, whereas Purple Team assessments are more comprehensive and use methods in several ways. This is to ensure detection capabilities are thoroughly tested and not easily bypassed by adjusting the exploit or attack in a trivial manner.
The image below illustrates how these compare to each other and shows how they stack up against Red Teaming.
How to start with Purple Teaming?
The image above shows that it is possible to start Purple Teaming using Atomic Testing frameworks. There are many out there to choose from with varying difficulty to use. I have listed a few below but these are not an exhaustive list.
- Caldera
- Atomic Red Team
- Mordor
- Guardicore Infection Monkey
- Purple Team Attack Automation
The above Atomic Testing frameworks can give you a decent starting point to assess and improve security posture. However, you should also spend time developing a repeatable and trackable methodology for planning, executing and reporting progress over time.
Larger businesses with their own Red and Blue Teams can start to build a Purple Team framework internally, or they may want to engage with a trusted partner to help build and execute an assessment program.
Initially, it can be beneficial to bring in the expertise of an organisation with both Red and Blue team skillsets to help get the program off the ground before slowly starting to develop an internal capability under its guidance.
Find out more about Purple Teaming and how Bridewell can help you proactively test your defensive capabilities by contacting a member of our Purple Team.
Author
Gavin Knapp
Cyber Defence Technical Lead



 Blogs
Blogs